Mobile Phone Spy App
Monitor calls, SMS, Gps, Camera, Photos, Videos, Whatsapp, Facebook, etc.
In fact, in addition to analyzing the implementation principles of java languages such as java internal classes and enumerations, it is also useful in some specific scenarios. Now it is generally done by modifying smali, but it can also be done based on bytecode., This article is based on the previous java bytecode analysis, so only the bytecode method is discussed.
Many stand-alone games, and even some online games, run the logic operations locally. The server only receives the operation results uploaded by the client. There are also some charging applications, in fact, the functions are all in the local code, only But it is to judge whether there is a payment, and if there is a payment, the function entry will be displayed.
If we can modify its code and change the upload result or the judgment of whether to pay to what we want, we can do whatever we want.
decompile
To modify the code logic of the application, we must first analyze what the original code logic is. However, since the code of the application is the private property of each company, unless the code is leaked, we generally cannot get it. So at this time We can only use decompilation techniques.
Mobile Phone Spy App
Monitor calls, SMS, Gps, Camera, Photos, Videos, Whatsapp, Facebook, etc.
If you go to the Internet to search for the decompilation technology of apk, you will probably find the following methods:
- Use the apktool tool to extract the apk
- Use the dex2jar tool to convert Android-optimized dex files into java classes
- Use the jd-gui tool to view the java code in the class
Such a cumbersome operation is actually outdated. I will introduce a one-click fool operation tool for everyone.
jadx is an open source Android decompilation tool, its code is hosted on github, you can download and use it. The usage is very simple, after downloading, unzip it, and then enter the bin directory to run jadx-gui (linux/mac) or jadx-gui. bat (windows), you can start a visual interface, then click "File - Open", and select the application we want to decompile, you can see the code in the apk
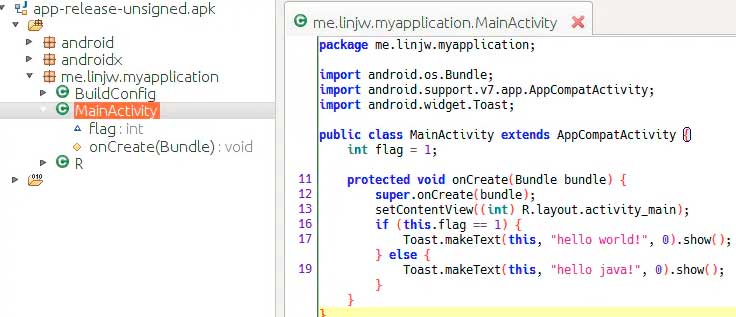
A demo application is decompiled here, and its MainActivity.onCreate judges a flag variable, and then pops up Toast. When we install this apk and run it, we can see the toast pops up: "hello world!"
Other applications are similar, you can view their code in this way. However, officially released applications generally do obfuscation operations. At this time, the class name, method name, and variable name of the code we decompile and process will become a, b, c is a meaningless character.
But only the name has changed, the execution logic is exactly the same, so as long as you are careful enough, you can still understand its code logic.
Jadx has a powerful function that can export gradle project, click "File/Save as Gradle Project" to export gradle project, and then change the directory structure, you can use Android studio to open the project and edit and modify the code.
If the compilation is successful after modification, then our purpose has been achieved and we can do whatever we want, but this project has a high probability of not being able to compile successfully, and there are many strange errors.
Next, I will take you to decipher this apk step by step, modify its logic, not play "hello world!" but play "hello java".

Modify the application's bytecode
We can use jadx to easily analyze the code logic, but if the recompilation fails, we have to go another way.
Here is the way to directly edit the bytecode. If you go this way, there will be no fool operations to use. Let's take it step by step honestly
1. Unzip the apk
- apk is actually a zip compressed package, we can change its suffix to.zip, and then decompress it directly
- We put the decompressed things into the app-release-unsigned directory:
2. Convert dex to jar
- We all know that the Android virtual machine is not an ordinary java virtual machine, it cannot directly run java class files, and needs to be optimized into dex files.
- When we modify the bytecode, we need to convert it back. Here we use the dex2jar function of the dex-tools tool:
- Here I only introduce the usage of commands under Linux, not on Windows. In fact, it is a similar version using.bat, you can search by yourself.
- Convert classes.dex to jar file:
- ~/dex-tools-2.1-SNAPSHOT/d2j-dex2jar.sh classes.dex
- It will generate classes-dex2jar.jar file:
3. Modify the class bytecode
- In fact, the jar file is also a zip compressed package, we can still directly change the suffix to zip, and then decompress to find MainActivity.class
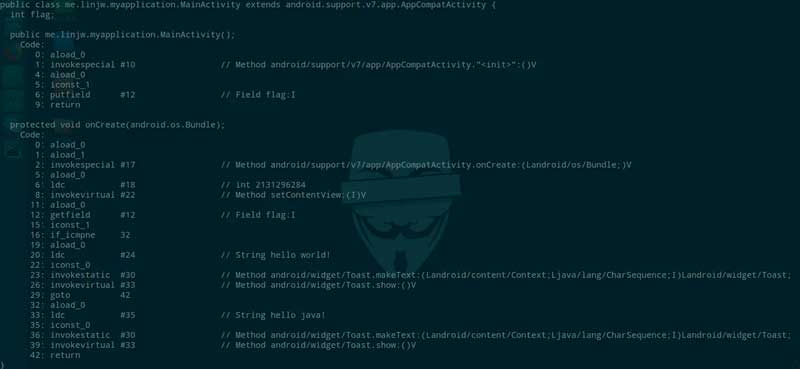
- At this time, we can use the javap command mentioned in the previous article to view the code inside:
- javap -c MainActivity
- And we can see that if we continue to execute, it will output hello world!, and if we jump to 32 lines, it will output hello java!
- Here we can directly change if_icmpne to if_icmpeq, jump to line 32 when it is equal, otherwise continue to execute, so the original "hello world!" prompt will become "hello java!"
- If you open the class file directly with an editor, there are some binary values in it.
- So how do we modify it?
- Here we will use another tool jbe, the full name is java bytecode editor
- After downloading, unzip it, enter the bin directory and use the following command to open the graphical interface:
- java ee.ioc.cs.jbe.browser.BrowserApplication
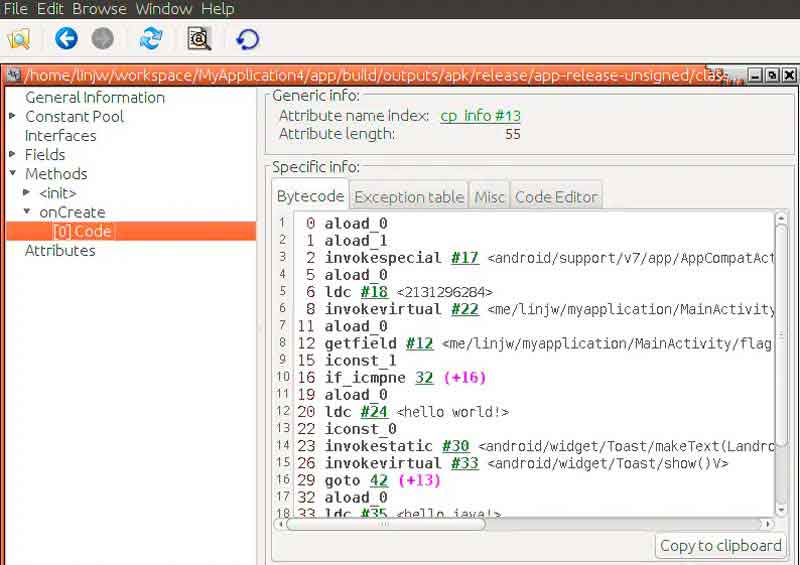
- Open MainActivity.class in the graphical interface and find our MainActivity.onCreate code
- Then click the Code Editor option to modify the bytecode, here we change if_icmpne to if_icmpeq, and then click Save method:
- This completes our logic modification
4. Repackage dex
- Next we will repackage the apk, first compress the class into a zip, pay attention to the directory structure:
- Then change the suffix to jar and use jar2dex to generate dex:
- ~/dex-tools-2.1-SNAPSHOT/d2j-jar2dex.sh classes-dex2jar.jar
- Then replace the original classes.dex with the generated dex, and then delete all the temporary files just generated, such as classes-dex2jar.zip and classes-dex2jar directories
5. Delete signature information
- Generally, the applications we get are signed applications. After the application is signed, the verification information of resources and codes will be saved in the apk. If we modify the dex file, the verification will fail, so the apk cannot be installed. of.
- So we need to delete the original signature. The specific method is to delete the three files in the META-INF directory:
- CERT.RSA
- CERT.SF
- MANIFEST.MF
6. Repackage apk
- Next, the same compressed file generates a zip compressed package, pay attention to the directory structure:
- Finally, change the zip suffix to apk, and our apk is packaged
- Since our repackaged apk has deleted the signature information, if it is installed directly, it will fail, and we need to re-sign it.
- You can use the following command to create alias as android.keystore, and the file name is also the signature file of android.keystore
- keytool -genkeypair -alias android.keystore -keyalg RSA -validity 400 -keystore android.keystore
- After pressing enter, it will let you enter some password, developer information, etc., and you will get an android.keystore file after completion
- Then we use the obtained android.keystore to re-sign the app:
- jarsigner -keystore android.keystore -signedjar release.apk app-release-unsigned.apk android.keystore
- Get the signed release.apk, let's install it and run it to see that the toast has become "hello java!".