What should I do if I have doubts about my partner, such as monitoring my partner's mobile phone? With the popularity of smartphones, there is now a more convenient way. In the past, mobile phones only had the function of making calls and sending text messages, but today's smart phones can not only locate, but also take pictures, record audio, synchronize address books, call records, and view text messages and other powerful monitoring functions.
If someone can have an unobstructed access to your mobile phone, which settings he can make on your mobile phone, and which applications he can even install to easily monitor you. Ordinary monitoring apps can enable the phone's anti-theft function that comes with the phone or security apps, and more powerful tracking apps can get most of your phone's monitoring permissions. If the other party uses this type of mobile phone application, they can easily check the location of the monitored mobile phone, call, text message, address book, photo album, and even perform remote photo taking, monitoring, recording, real-time screenshots, real-time voice, and other operations such as viewing the mobile phone screen.

I don't know when, the "mobile phone anti-theft function" has been equipped as standard in smart phones. At that time, it became a useless function in Android mobile phones. For accidentally lost mobile phones, there is still a chance to find them back. For stolen mobile phones, thieves can easily kill this anti-theft setting by simply shutting down and flashing the phone ( At present, some customized Android systems have adopted the anti-swiping function), but this anti-theft function has become a sharp tool for tracking the owner of the mobile phone.

How to turn on the anti-theft function of the mobile phone, most of the customized Android systems in most mobile phones have this function as standard, as long as the corresponding account is opened on the mobile phone and logged in, the anti-theft function of the mobile phone can be turned on.
What can the mobile phone anti-theft function do? The most basic thing is positioning. Check the current geographical location of the mobile phone, and use the GPS or mobile base station positioning method of the mobile phone. Although the location is not very accurate, it is still accurate. At least you can know your approximate in which building.
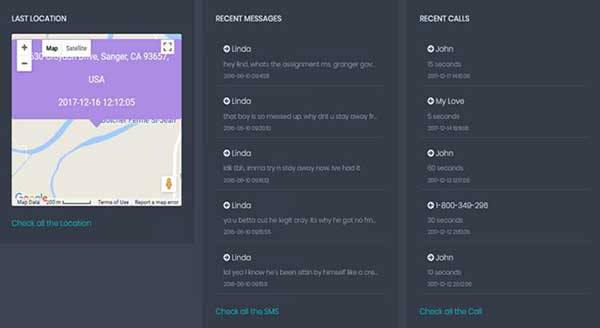
In addition to mobile phone anti-theft, smart phones also have cloud synchronization function, which can synchronize user photo albums, address books, call records, text messages, etc. in real time. content on the server. (Since the leak, some manufacturers currently need to verify the text message after logging in to the cloud synchronization function to view the corresponding content).
The openness of the Android system makes many mobile applications unscrupulous. The most basic thing for a mobile application is to obtain the list of applications installed in the user's mobile phone, the user's location, and some applications also obtain permission to read the address book, text messages, and take pictures. Recording, collecting user operating habits, etc., obtained this information and even silently uploaded it to the server.
Surveillance App: Your actions are all seen clearly
Monitoring applications can be installed on your mobile phone in a few minutes
The emergence of a series of anti-derailment monitoring applications can make your mobile phone a complete monitoring tool. The user purchases a mobile phone monitoring application and installs it in the target mobile phone to easily view the location, calls, text messages, address book, photo album of the monitored mobile phone, and even remotely take pictures, monitor, record, and capture screenshots in real time, real-time voice, real-time viewing of mobile phone screen and other operations. This kind of mobile phone application is very intimate, and it is divided into Android version and Apple version. However, due to the closed nature of ios, it needs to be jailbroken before it can be installed and used, which limits its scope of use. For the Android system, most functions can be realized without root system, and full functions can be realized after granting root authority.
Others only need to get your mobile phone, install the corresponding mobile phone monitoring application, and then perform a series of configurations to deploy it easily. It only takes a few minutes to complete. Moreover, these mobile applications still run in hidden mode. When you operate the mobile phone daily, you can't even detect its existence on the mobile desktop and application list. It silently monitors every move of your mobile phone in the background. Some even put on a legal cloak to avoid killing by mobile phone security applications.
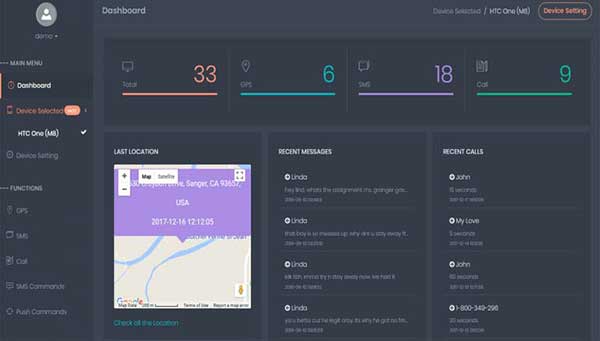
This type of mobile phone monitoring application has very powerful basic functions: real-time positioning of the mobile phone, viewing of address books, call records, text messages, chat records, photo transmission of front and rear cameras, call recording and environmental recording, screenshots and real-time screen recordings. Dynamic display, access to mobile phone files, etc., and value-added functions even include intercepting account passwords of third-party mobile phone applications, intercepting text messages, etc. That is to say, the other party can get all the content in your mobile phone anywhere, as if they are operating their own mobile phone. After the user logs in, the user needs to set the binding mobile phone. It should be noted that if the number a (the control terminal) is bound to the number b (the controlled terminal), then as long as the number b is logged in any mobile phone, it can be directly controlled remotely without having to do it again. scan code binding operation. After that, you will enter the main operation interface. After binding other mobile phones, you can switch to the control panel state of the controlled mobile phone.
From the control panel, you can see its basic functions. After installing the application in the controlled mobile phone, the controller can use it to remotely obtain the controlled mobile phone:
The application also has the option to hide the desktop icon function. The controlled user will not see the application on the mobile phone desktop or application list, and will not be aware of the application. This can only be seen in the application management in the settings center application exists. The controlled user does not need any operation, and there will be no prompts on the screen. Even if the controlled user turns off the screen, the controller can easily connect to the video and view the real-time content of the controlled user's front and rear cameras. In other words, the controller can check your every move through the phone camera at any time. Although the controlled end can block some remote control functions through settings, this is based on the knowledge of the controlled end.
After reading this article, I was a little terrified, so how can I check whether my mobile phone has been installed with a monitoring application? I am sorry to tell you that because some monitoring applications are very good at disguising, and security applications turn a blind eye to some monitoring applications (at least remind users of risky applications!), so non-professionals, you can only track based on some clues.
For a partner, in addition to loyalty, communication is also needed, and more importantly, trust and cherishment are needed. Obtaining each other's every move through monitoring is itself a heavy burden for both parties. You need to prevent your mobile phone from being monitored. In addition to not installing mobile applications at will, you also need to add a lock screen password to your mobile phone and try not to root or jailbreak. Android users should not enable the USB debugging function of your mobile phone, so that even if others get your mobile phone, nor can you install other applications on your mobile phone.
How to see other people's phone screen, call history, sms, conversation, text messages, email, gps location, call recording, photos, whatsapp, messenger, facebook.The mobile spy app can remotely monitor and track my partner's android phone. Download spy app for free and install apk file on target cell phone.Best spy software - Find and locate someone's phone online, read phone message from husband or wife on another cell phone.